
This writeup is that of the OSINT task of this CTF.
OSINT [500 pts]
Task description:
Catch me if you can
Solution:
The email provided (TheBox.eml) can be opened and viewed using Microsoft Outlook or ThunderBird:
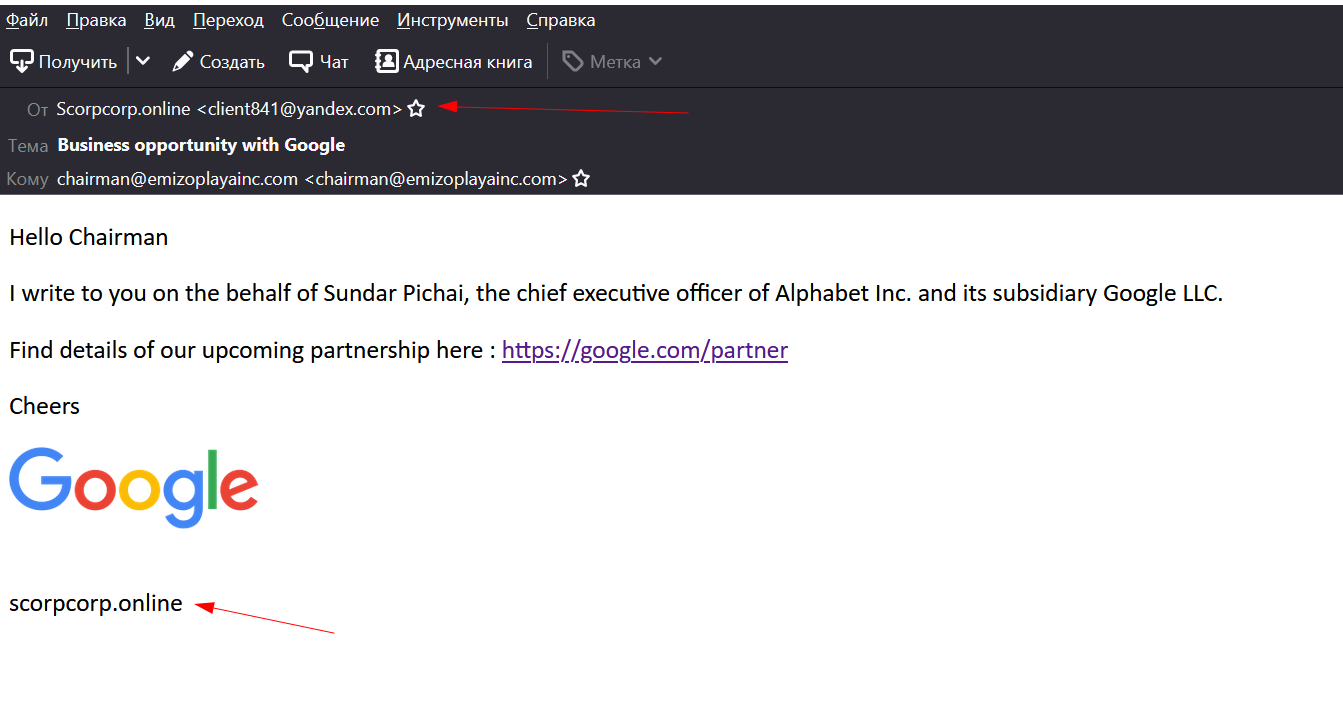
So, the sender ([email protected]) claims to be writing this email to [email protected] on behalf of Sundar Pichai.
NB: This should be flagged as suspicious, because, why would an employee of Alphabet Inc send a business email using their personal email and not a business email (which should be of the form [email protected] for example).
So, we got two IOCs: scorpcorp.online and [email protected]. Researching this email online didn’t yield anything; so, we had to focus on the scorpcorp.online. On the website’s main page, we see the website’s designer name (Glenn Benola):
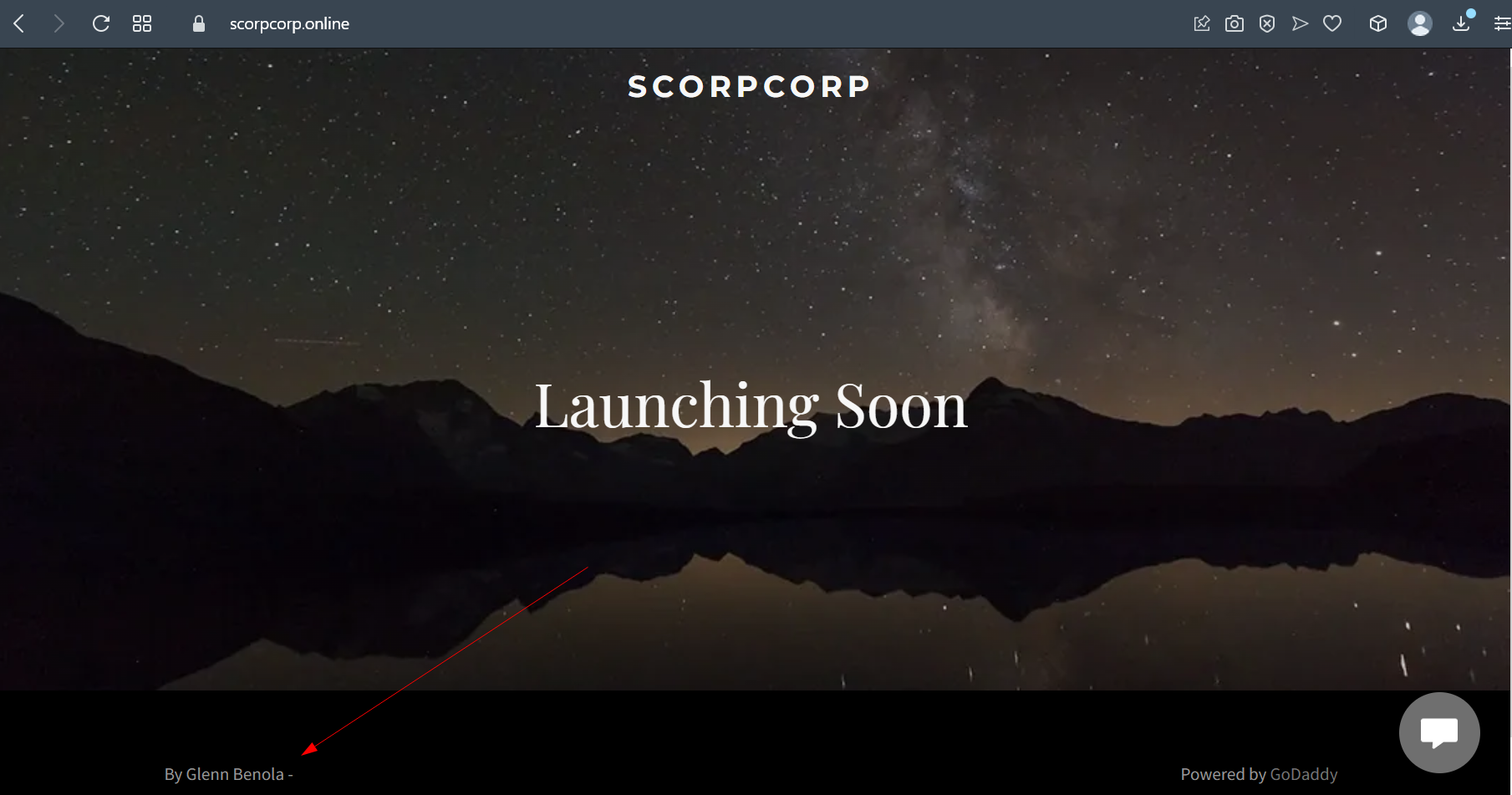
A quick Google search of “Glenn Benola” directs us to the Twitter page https://twitter.com/benolaglen:
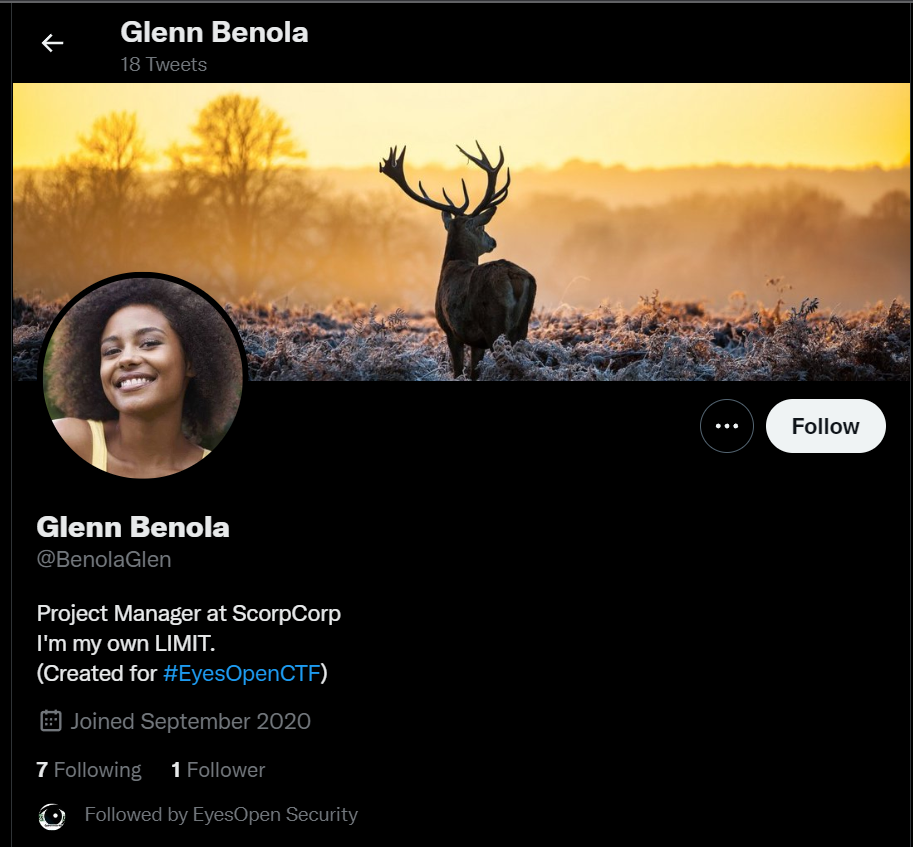
One of the Glenn’s tweet was aHR0cHM6Ly9qdXN0cGFzdGUubWUvSktvSA==. Decoding this Base64 encoded text yields the pastebin link: https://justpaste.me/JKoH.
That pastebin contains the base64 string of a PNG. We then copy the string to a new file (say tmp.txt) on our computer, while making sure to remove the string “data:image/png;base64,”. We then decode the base64 encoded image:
cat tmp.txt |base64 -d > image.png
(or you can use an online tool to decode your string)
The image (image.png) is a QR code. Scanning the code, we get the link: https://yadi.sk/d/RPwGjZZ6z3Sd5w?w=1. The file named “scorpcorp-secret-eoctf” was hosted at that location. Download the file, then look at its metadata and you will see the flag:
flag{osint2420}
