
P.S. I initially published this article on medium on 19.10.2019.
Disclaimer: I am a newbie in the security field. In fact, I am a noob (as rightly said on HTB), so I still got a long and hopefully interesting journey. The following might be quite basics or boring for some of you experts out there, but I hope to get some criticism from you, and why not reach other newbies like myself. And also, to keep it authentic, the slides are maintained in their original language, which is French
A few weeks ago, I learned the basics of phishing analysis and threat intelligence via an online competition and training event titled Operation Chimera (which I highly recommend to you). Little did I know, I was going to apply the skills acquired in a real-life scenario.
Some time ago, a close relative sent me a link (http://malomit[.]com/canada) for a Canadian Visa Lottery. It was quite intriguing to me because, I had never heard of such a thing. To my knowledge, only the US is does that. But that wasn’t a solid point, so I decided to dig into it. That is when the fun began 😃.
For this analysis, I used a certain number of free online tools which I will briefly present:
- URL2png: This allows you to view the front/main page of a website without visiting it or clicking on the link. In addition, it allows you to zoom desired portions, thereby enabling you to read the content of the home page.
- Urlscan.io: It does a similar work as URL2png, but got some pros and cons. The main con is that you can’t zoom the outputted photograph, thus making it difficult to read the websites front page. Nevertheless, it gives you all the other links present on that web page, the various IP addresses involved in HTTP requests and much more.
- Wanna Browser: This is an amazing tool: it allows you to view the source code of a website without browsing it. In case you are familiar with web development, you would be able to flag any malicious code or links embedded.
- Virustotal: This is an antivirus software used to inspect blacklisted domains, files (hashes), IP addresses, URLs, etc.
Remark: Throughout my analysis, I avoided clicking on the link to protect myself from a drive-by download attack. Briefly, a drive-by download refers to the unintentional download of malicious code to your computer or mobile device that leaves you open to a cyber attack. That is, you don’t have to press download, or open a malicious email attachment to become infected: just clicking on the link is enough.
Let’s now dive into the analysis itself:
Firstly, I tried getting the home page of the website using URL2png and it looked as such:

Nothing alarming, right? let’s proceed!
Next, I went through the website’s source code and I noticed a bunch of intriguing features:
- The sender tended to speak in an informal way, which any serious government entity won’t do. At some point, the sender wrote: I thank you very much
- Going through the source code: normally, the available number of VISA is supposed to vary based on the number of already issued VISA. But surprisingly, there was no counter to take care of that! That is, the number of VISA was hard-coded as plain text. That was weird and alarming! Anyways, I proceeded;
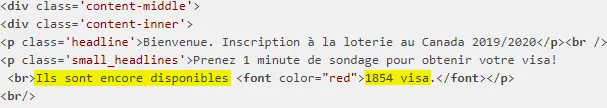
-
In addition, at no point in time were the applicants asked their name, surname or any other similar information like in the US lottery. That is, all they needed to precise was their gender, social status, age range and that was all to get a VISA! Pretty funny, right? I just smiled and got excited, as I was about to stop a bad guy. From there, I classified the attacker as an amateur.
-
Next, the applicants were obliged to share the link with 5 other people in order to submit their applications. But, what’s the essence of doing that? I asked myself.
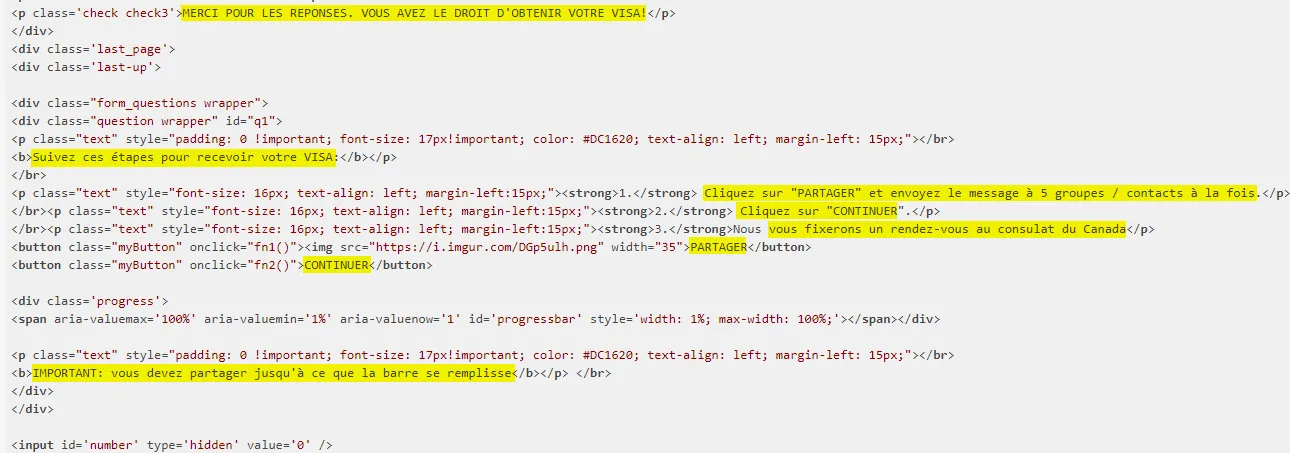
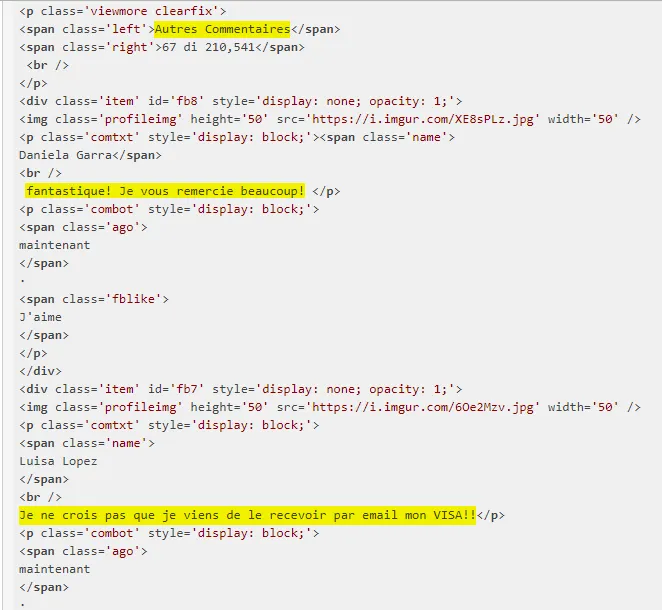
- As if it wasn’t enough, the sender pretended the applicants will receive their VISA via email. We are in the 21st century, and I guess this isn’t yet possible (feel free to correct me if I’m wrong). In addition, he never asked the applicants email addresses. So, how was he going to do that? that remains a mystery. They even added some fake comments, testifying the legitimacy of the lottery (thereby luring more and more people).
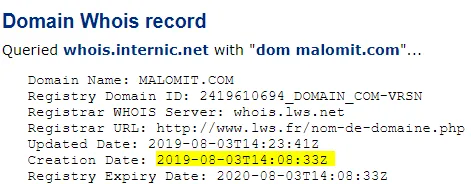
Furthermore, the main IP address was in the US and didn’t fall in the range of IP addresses assigned to Canada. You may be thinking it shouldn’t be alarming, as the company might have used a VPN (or any other similar service). But, why would a government entity hide its location for just a lottery? At this point in time, I had already categorized the URL as malicious. Next, I used Virustotal to check if the link wasn’t already classified as malicious (though that was supposed to be my first step), but it wasn’t the case. I got shocked, as it wasn’t even a sophisticated attack. After making a WHOis lookup, I got the answer to my question: in fact, the domain was only purchased roughly two months ago; That is, it was still brand new.
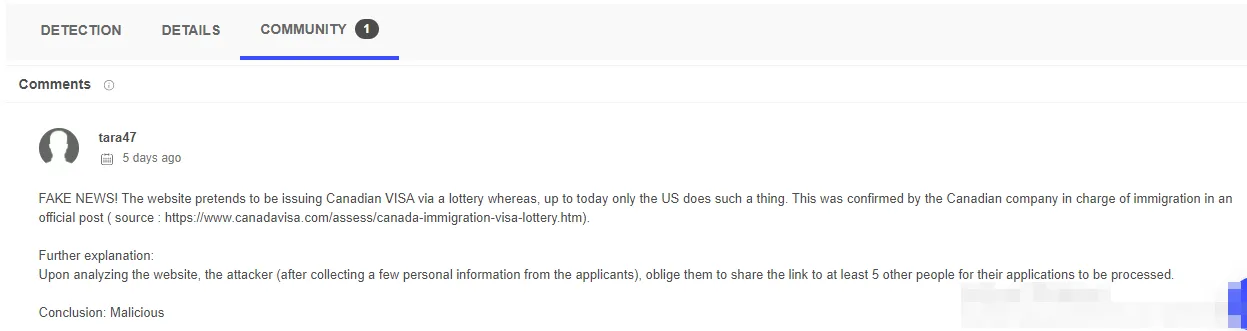
After googling a little bit, my doubts were confirmed: the Canadian company in charge of immigration clearly mentioned in an official post that Canada do not issue VISA up on a lottery. They thereby asked the general public to be on their guards, as there are a lot of websites out there claiming the contrary. (Source: https://www.canadavisa.com/assess/canada-immigration-visa-lottery.htm)
Before I conclude, there is something I need to point out here: I really don’t know anything about web development (for now), so the attacker could have embedded some malicious code or links without me noticing it. Finally, I reported the website as malicious on Virustotal via a comment.
I think we can at least pull out a lesson from this: DO NOT CLICK ON LINKS RANDOMLY, whether they are from close relatives or not (as usually they themselvesaren’t aware of the risks). Prevention is better than cure! Hope you learned something and any criticism (technical or not) on my analysis would be highly appreciated. STAY SAFE! `
